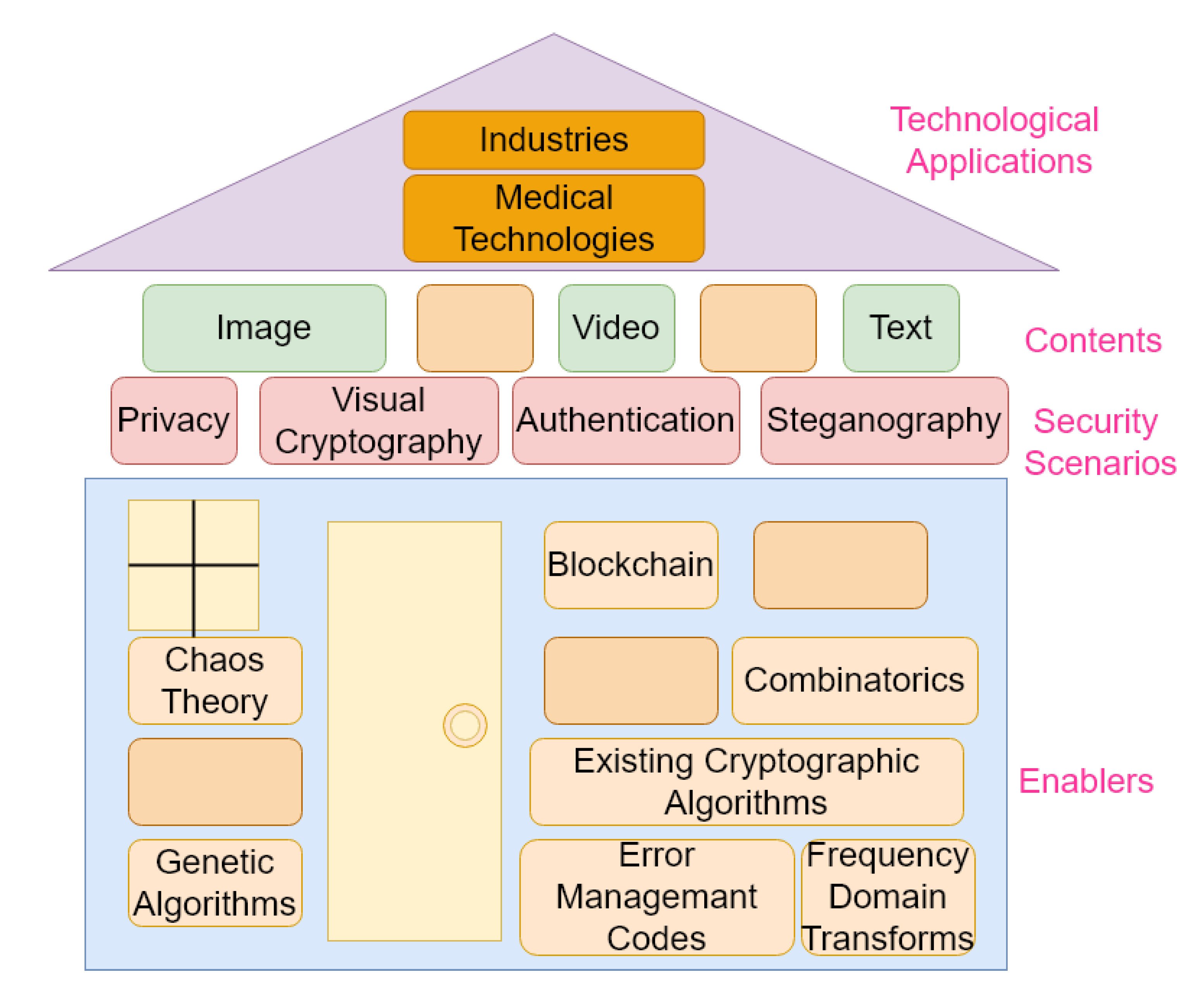
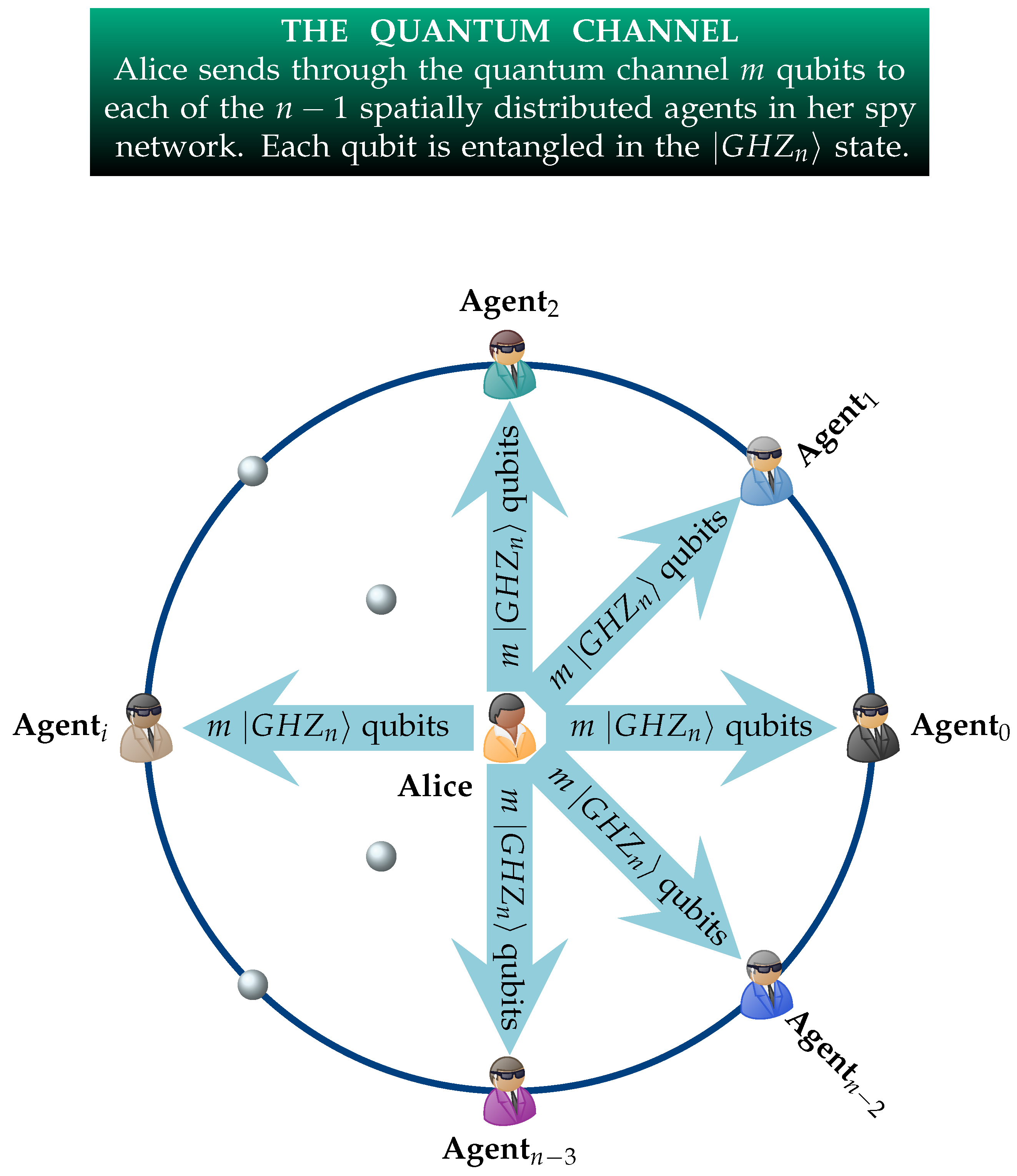
Sustainability | Free Full-Text | Quantum Key Distribution Protocol Selector Based on Machine Learning for Next-Generation Networks
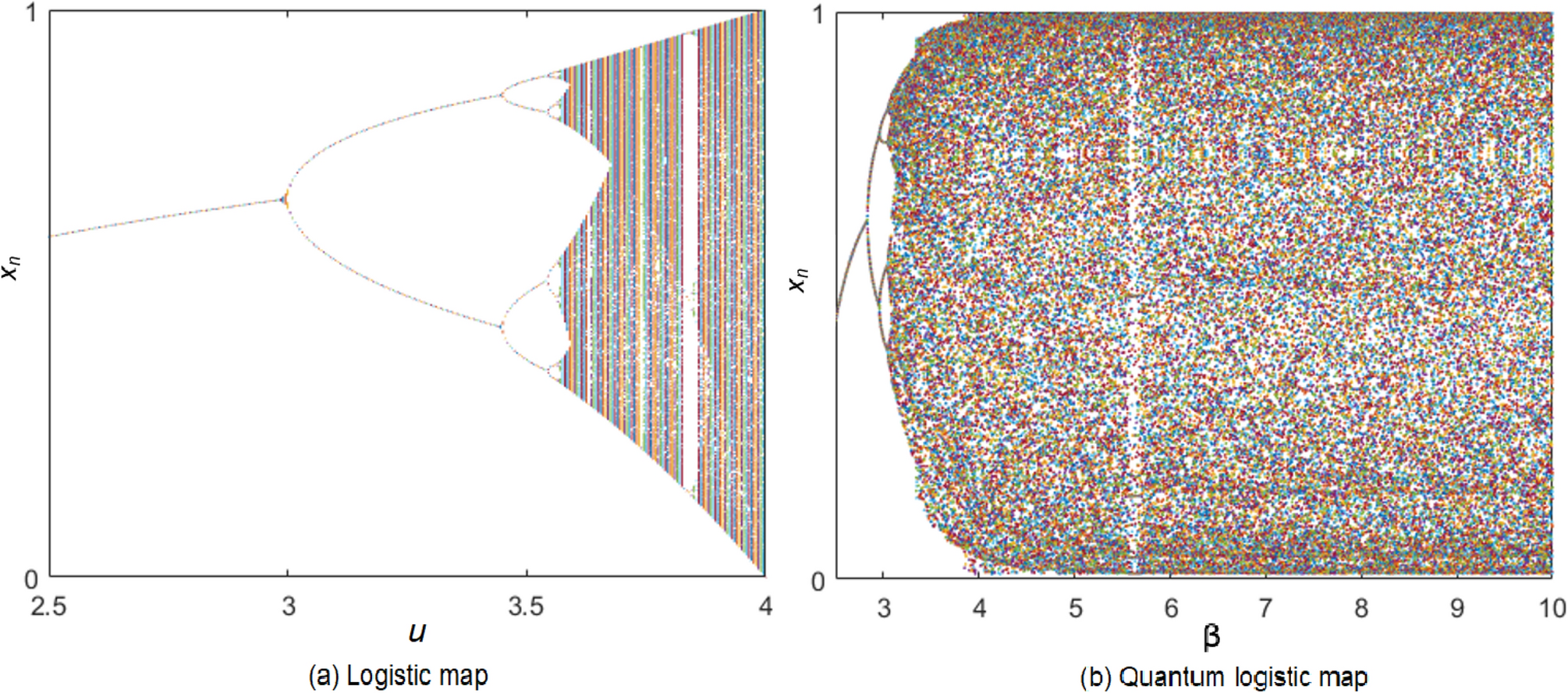
An image encryption scheme based on public key cryptosystem and quantum logistic map | Scientific Reports
A NOVEL CRYPTOSYSTEM BASED ON ABSTRACT AUTOMATA AND LATIN CUBES∗ 1. Introduction Automata theory provides a natural basis for
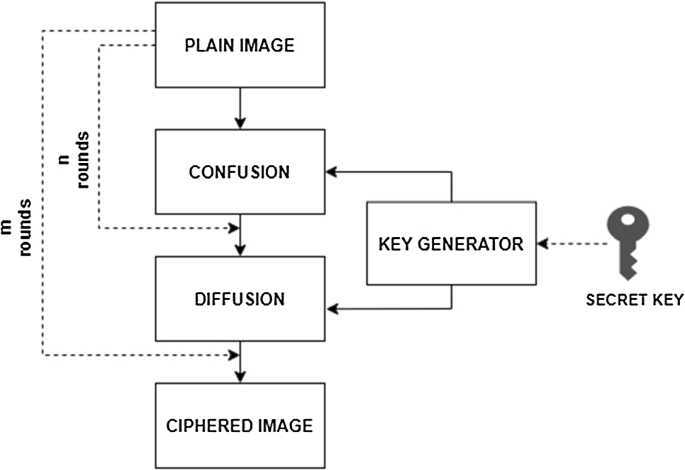
Survey on image encryption techniques using chaotic maps in spatial, transform and spatiotemporal domains | SpringerLink
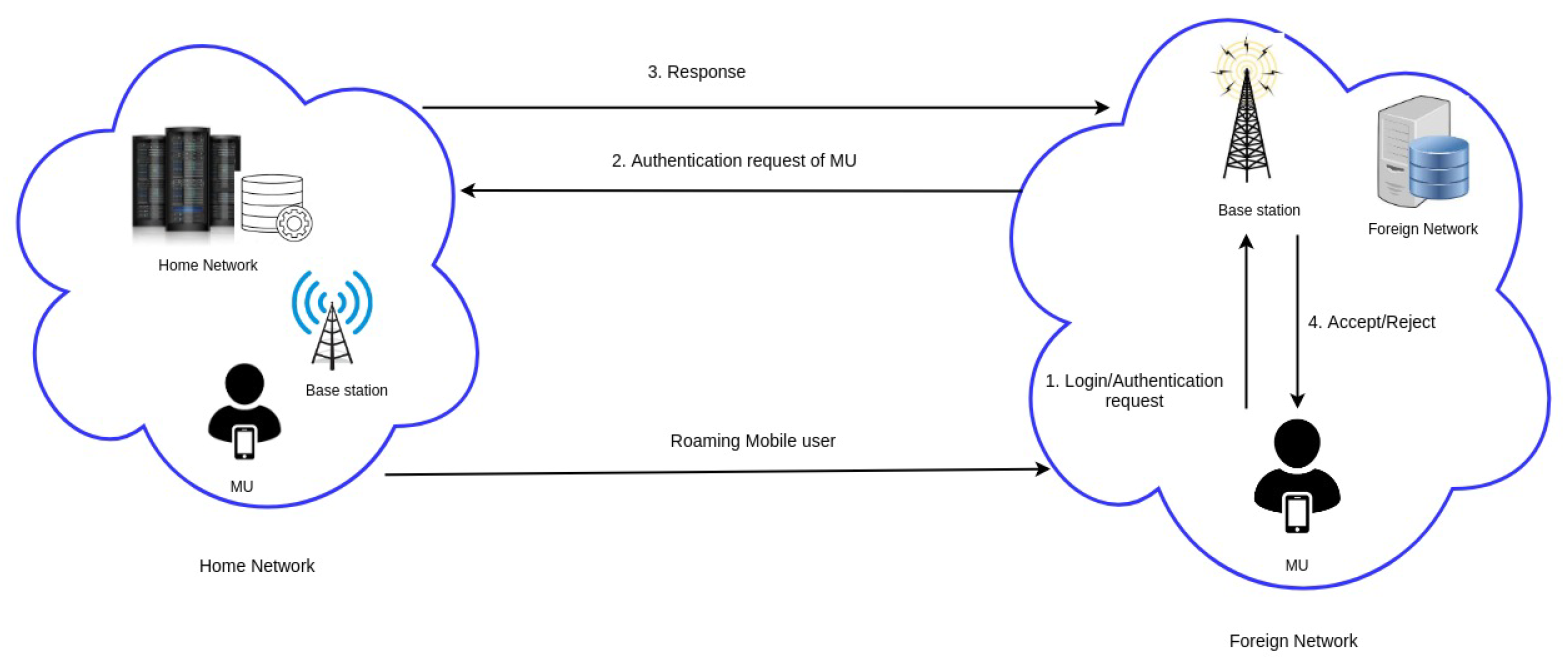
Cryptography | Free Full-Text | ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks

Correspondence between cellular automata and cryptography according to... | Download Scientific Diagram
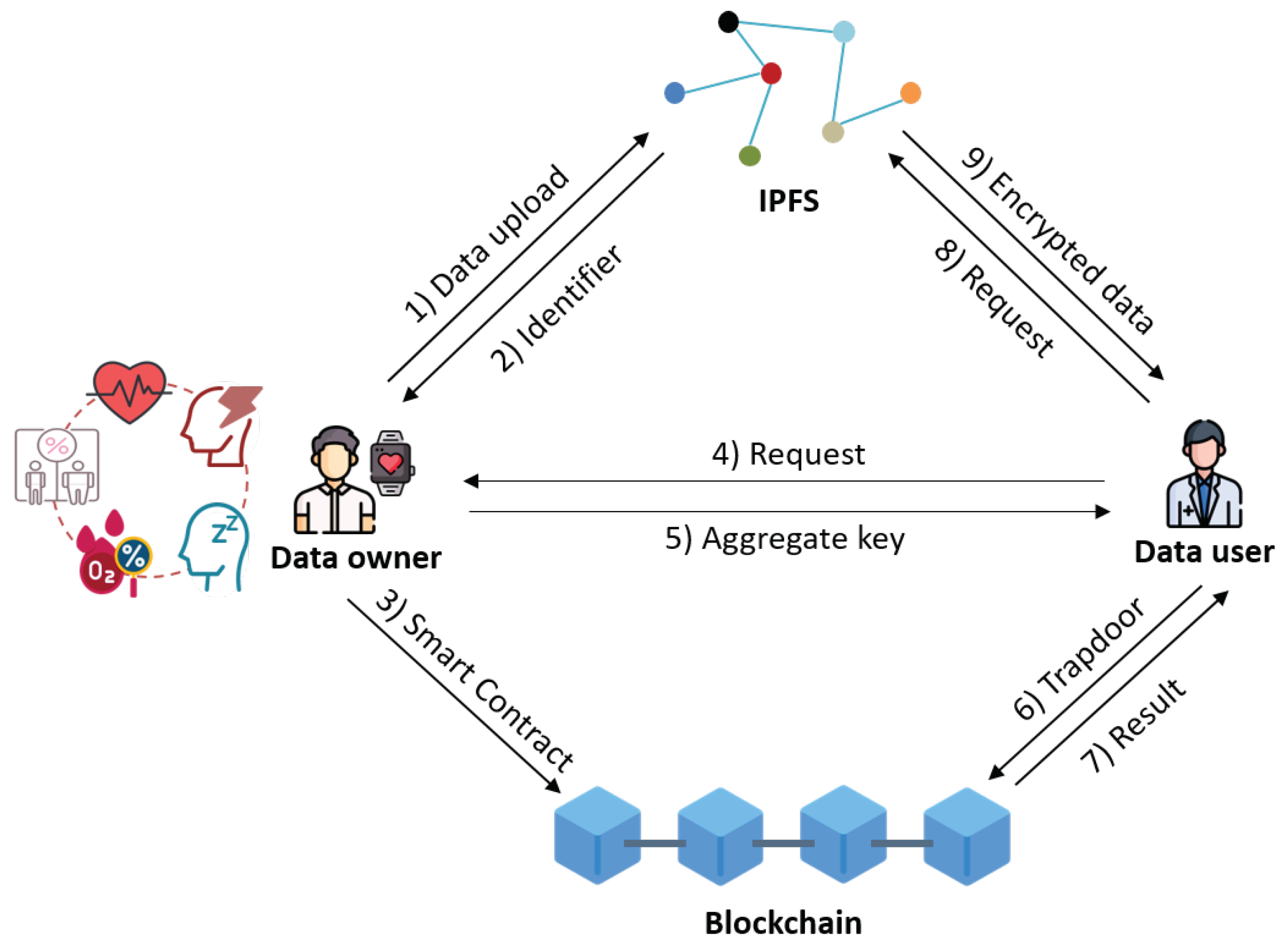
Electronics | Free Full-Text | A Secure Personal Health Record Sharing System with Key Aggregate Dynamic Searchable Encryption




![PDF] Cellular Automata and Cryptography | Semantic Scholar PDF] Cellular Automata and Cryptography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/513f8c667fa015879356692c3e98f4fb8d052303/29-Figure2.5-1.png)