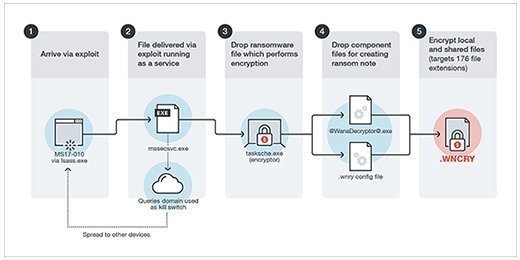
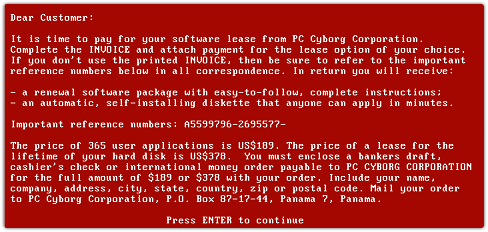
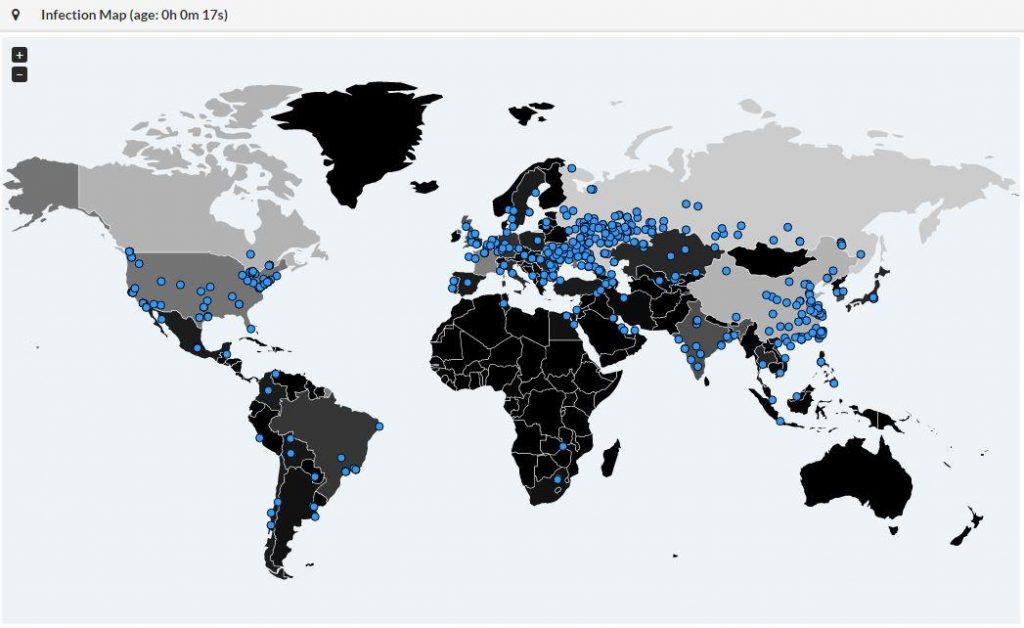
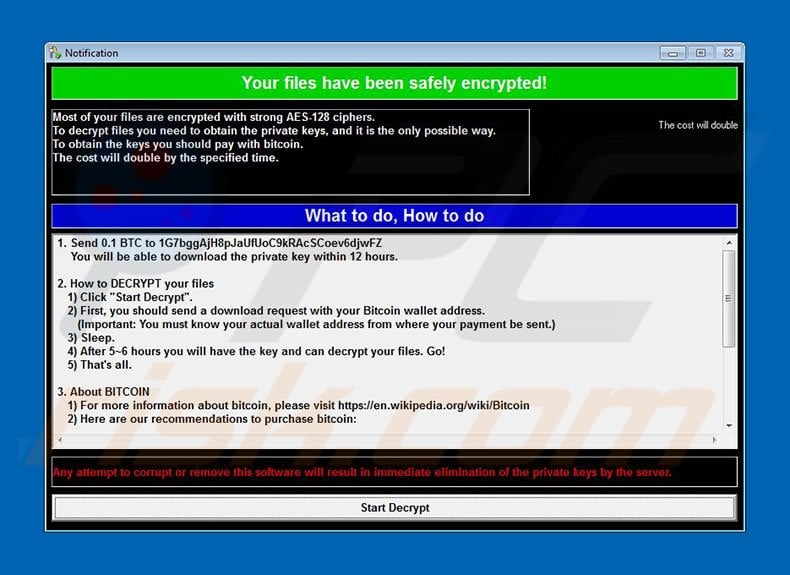
WannaCry: Companies bolster cyber defenses for new ransomware attacks | Technology News,The Indian Express

Windows XP, Server 2003, Windows 8 RT: Emergency Security Updates & Fixes For Wannacry - TechNet Articles - United States (English) - TechNet Wiki